Your customer asks you for proof of the TISAX® label. What now?
There it is, the information from your customer that you or your company should now please provide proof of a TISAX® label.
Now the question arises as to what exactly needs to be done, which departments need to be involved and how the process for a successful assessment according to TISAX® actually works in order to meet the customer’s requirements.
Here is a short guide for orientation:
TISAX®, the standard for information security in the automotive industry, is a common assessment and exchange mechanism that makes the findings from information security assessments accessible to all manufacturers. The results of the tests are mapped in a maturity model. Recertification is generally carried out every three years or, for example, if the participating company wishes to demonstrate a further audit objective or if a major organizational change has taken place.
To cut a long story short: If a customer requests proof of the TISAX® label, proof of TISAX is usually mandatory. However, if you do not receive customer data or do not have access to the customer’s systems, then in very rare cases the customer’s request may be unfounded.
You should also check at which locations the actual service provision that makes the TISAX® assessment necessary takes place. For example, if you have several locations in your company but do not produce/provide the service at all of these locations, then only those at which the service is provided for the OEM must provide evidence of the TISAX® label.
Depending on the size of the company and the assessment objectives, a time frame of at least 6 months should be planned for a successful TISAX® assessment. Depending on the resources available and day-to-day business, for example, this can of course take up to 18 months. TISAX® is therefore not “just done on the side”.
TISAX® is the standard for information security in the automotive industry. It therefore makes sense to integrate members into the team who have knowledge of your company’s IT and information security processes as well as employees who have expertise in internal project management areas and are characterized by strong communication skills. In other words, employees from all areas of your company in which values (information in digital or physical form, prototypes) are used and passed on.
If your company already has an integrated information security management system (ISMS for short) that is practiced by all employees, this greatly simplifies the implementation of the TISAX assessment. If no ISMS is in place, the required documentation must be prepared in accordance with the audit objectives.
We have outlined the actual process of the TISAX® assessment for you here:
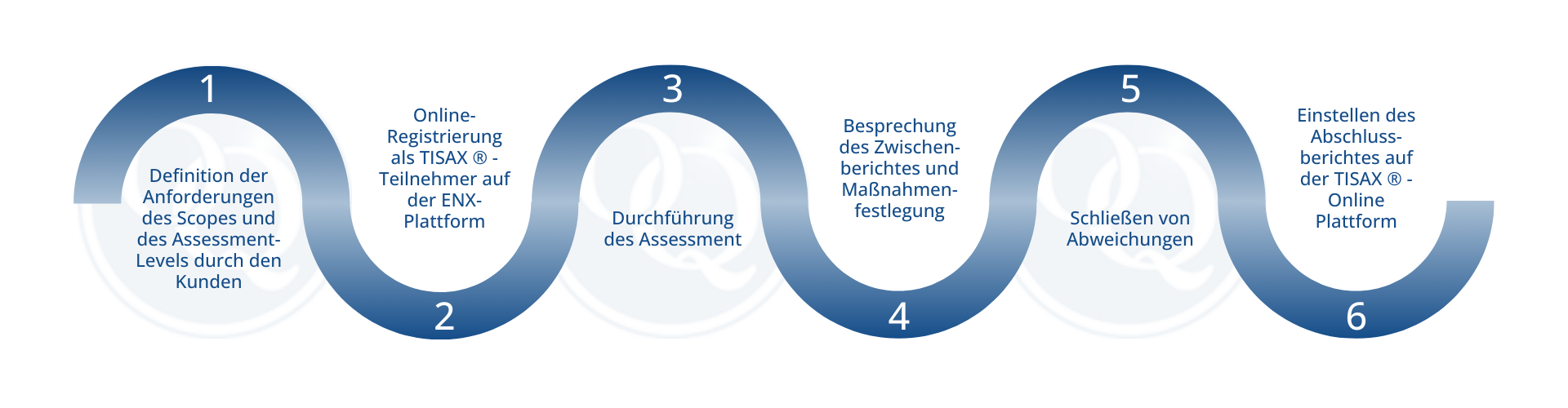
The resources required are too individual to be generalized. As mentioned above, an existing ISMS, for example, simplifies the TISAX® assessment, as the necessary documentation is already provided in advance. In order to be able to estimate the effort required for the TISAX® label in advance, GAP analysis tools can be used to transparently present the status quo within the company in relation to the target status. The resulting strategic and operational gaps then provide information on the required resources in the evaluation.
Our TISAX® experts at OPTIQUM will be happy to advise you.
TISAX® is basically aimed at all suppliers and service providers in the automotive industry who need to protect sensitive data and information – both their own and that of their customers – in the best possible way and regularly provide evidence of this by means of documentation.
The security of the exchange of information must be ensured throughout the entire supply chain and the scope of testing is based on the respective customer-specific requirements. The famous stone making waves in the water serves as an analogy: All participants who come into contact with the respective sensitive data are affected by the waves and must therefore guarantee the responsible and secure handling of the information in question.
However, the TISAX® certificate can also be seen as an added value for the partner companies in the supply chain: In an existing collaboration with external companies, for example, which access and use the internal data center, mutual information security is the highest priority for a strong, trusting cooperation.
If you have little or no experience in the field of information security, it is advisable to consult an experienced TISAX® expert. A workshop is worthwhile here to clarify open questions in advance, gain insights into TISAX® and information security and define your own strategy for the TISAX® assessment. The customer-specific requirements and scopes must be precisely identified, evaluated, analyzed and brought together in both the IT and production areas – it is therefore worth getting a partner with the relevant TISAX® expertise on board to work efficiently and strategically towards the successful TISAX® label.

Please contact us:



